Let's improve ours Crypto investigations with MetaSleuth

In Anthony F. Janson's work, History of art, the following statement is attributed to the absolute genius Leonardo da Vinci, referring to a poet who…
Read more →
In Anthony F. Janson's work, History of art, the following statement is attributed to the absolute genius Leonardo da Vinci, referring to a poet who…
Read more →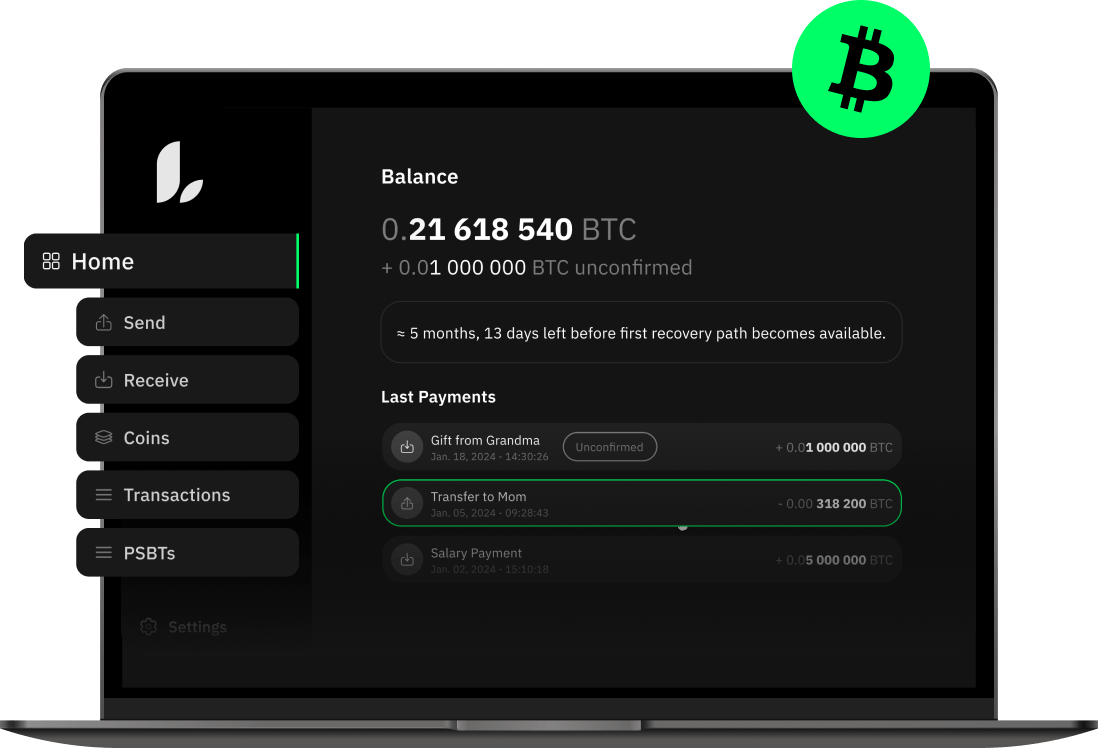
Tools like Liana, which is described in this post, are designed for experienced users. If you are not sure about how it works and how…
Read more →
In a previous post, we illustrated our Blind Protocol, which allows two operators to create a paper wallet splitting the private key so that nobody…
Read more →
It might happen that we want to share some kind of information with a third party without the need to writing down the information in…
Read more →
In some cases it may be necessary to create private keys to securely store funds for others, for instance, when seizing cryptocurrency for the judicial…
Read more →
Generating private keys is perhaps the most delicate aspect in relation to the custody of cryptocurrencies. There are a lot of methods to obtain keys,…
Read more →