Recover access to a wallet file with AnuBitux

It is a weird thing but we may forget our wallet's password. Of course, we could use our mnemonic seed to recover it, but there could also be other cases in which we could be looking for a wallet's password. Let's see how we could recover access to the wallet with AnuBitux, using btcrecover.
What is btcrecover?
In AnuBitux, we can find btcrecover in the AnuBitux menu, under the "Recovery" section. This will show only a hint about how to use it because it has no user interface and needs to be run in our command line. It is a very powerful python tool that gives us a lot of different solutions to recover access to our wallets. It works with wallet files of many different clients (like Electrum, BitcoinCore, Coinomi, MetaMask, etc.), encrypted private keys, bip39 seeds with a passphrase, and more. Here you can find the official documentation about its password recovery features.
How to use it with AnuBitux
Let's assume we have a wallet file we do not remember the password. First of all, we need to prepare a list of passwords we want to try. We can do it by writing a list of possible passwords, using a prepared dictionary, exporting passwords from other available sources like mobiles, browsers, password managers, etc.
For our purpose we are using a small custom list, just to test how the tool works and a prepared Electrum wallet file. Electrum wallet files can usually be found in the /home/anubitux/.electrum/wallets directory. Notice that with Linux operating systems folders and files whose name starts with "." are hidden and may not be shown if the specific option is disabled.
It can be useful to place a copy of the wallet file we are trying to unlock in a separate folder, to avoid any accidental malfunction and risk to corrupt the original copy of the file. In our case, it is placed in the Documents folder.
Now let's try to unlock the wallet file running btcrecover. We have to use the --wallet option to indicate the path to the wallet file and --passwordlist to indicate the text file containing the passwords we want to try.
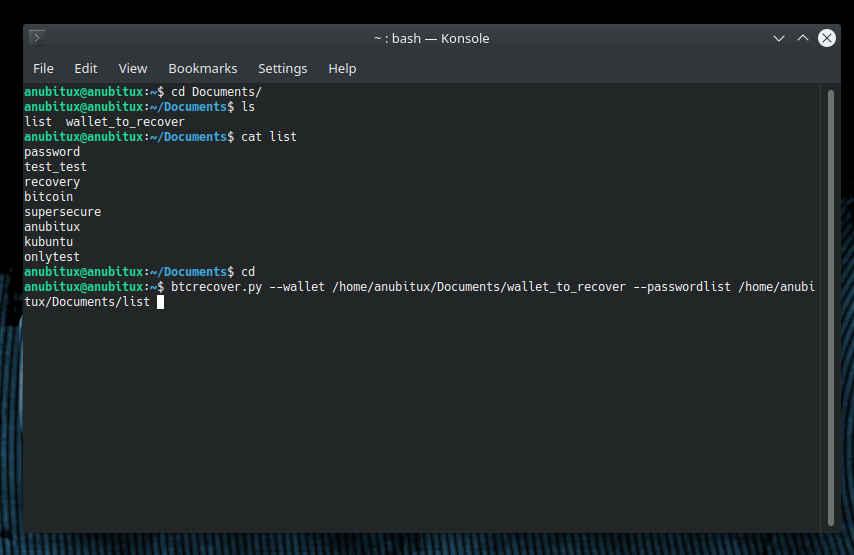
We could also use shorter paths to file, like "Documents/wallet_to_recover". So the command would be: btcrecover.py --wallet Documents/wallet_to_recover --passwordlist Documents/list. We could also move to the directory containing the files we need, using the cd command, and run the tool from there.
Now clicking Enter, the tool is going to load the password list and identify the kind of wallet file. Then it will start trying all the words until it finds the right one.
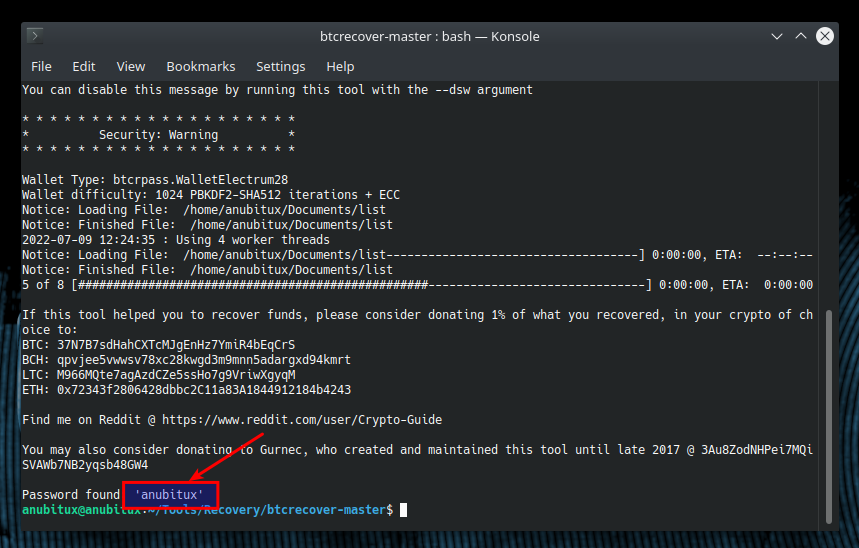
As we can see in the picture, the tool found the correct password in a few seconds, even because in this case we were trying only a list of eight words and the fifth was the correct one.
Some advice
As it is possible to see in the output of the tool, in the first stage it loads the whole file containing the password list. If we are attempting to brute-force a wallet with a big dictionary, it could saturate the RAM causing running issues in the whole running system. To avoid this kind of issue, it could be a good idea to split the text file into multiple smaller files. We can do that with the split command, like in the following examples:
split -l 10000 whole_list partial_list
This will create a set of files, which name starts with "partial_list", each one containing 10000 lines.
split -b 100M whole_list partial_list
This will create a set of files, which name starts with "partial_list", each one with a size of 100 MB.

