From wax tablets to elliptical curves. A Brief History of Cryptography (Part Three)

At the end of this brief journey through incomprehensible digits and letters (in case you haven't already done so, I suggest reading the first and second parts), in this article we will talk about a cryptographic method that has had great resonance in recent years, even thanks to the implementation in the Bitcoin protocol.
Without pretending to be able to liquidate the subject of cryptography in such small spaces, since such a vast and complex subject certainly goes beyond the purpose of these articles, I leave ample space for the passion and study of each of us on texts also available online.
This concluding article wants us to get to know a little better how a cryptographic method that is very popular and discussed today works: the use of Elliptic-Curve Cryptography in the Bitcoin protocol.
Some preliminary information
If we wanted to use a similarity with the traditional credit system, we could think, simplifying to a minimum, that in the Bitcoin system the public address represents a sort of Iban code, the wallet is the credit institution or a safety deposit box and the private address depicts the secret code to access the account or the key used to open the safety deposit box.
Choosing a wallet is one of the first operations to be carried out to enter the world of cryptocurrencies and is equivalent to opening a virtual wallet, which acts as a container for one's bitcoin addresses.
There are various types of wallets, each with its advantages and disadvantages, depending on whether you want to use it on a computer, smartphone or directly online, in the latter case without installing any program. This first category is known in the jargon as hot wallets, because it is based on applications that are somehow connected to the internet.
Conversely, cold wallets or cold storages are considered much more secure since they are not connected to the internet. This category includes wallets stored on an external mass memory and kept in a safe place, or the so-called hardware wallets, hardware devices created specifically to store private addresses.
Among the cold wallets we can certainly mention the physical bitcoins, real coins minted in metals of different values, inside which the numerical representation of the private bitcoin address is printed and kept.
Finally, one of the methods considered among the safest for storing bitcoin addresses is the paper wallet, i.e. the simple printing of bitcoin addresses on paper, perhaps even in QR Code format to facilitate their use, to be kept in a safe place.
Although the cold wallet category is generally considered more secure, since it is not exposed to any pitfalls deriving from connection to a network, it must be borne in mind that the loss of one of the aforementioned devices results in the almost certain loss of the bitcoins contained in them.
All these applications and devices have, as their main purpose, the preservation of bitcoin addresses, in particular the private one on which the existence of both the public address and the bitcoins themselves depend.
The Bitcoin protocol
We all know by now that the Bitcoin system is based on the invention of what we can define as the backbone of this protocol, which is the Blockchain.
Beyond what the use (and abuse, I would add) of this excellent intuition has become today, it will be necessary to remember that for the Bitcoin system to guarantee secure transactions between users, without the presence of intermediaries who act as guarantors, the creators took advantage of the important developments in cryptography, especially public-key cryptography.
In fact, the first approach to the Bitcoin world takes place with the creation of one's own key pair, the public and the private one, linked together through a one-way cryptographic function called the Elliptic Curve Digital Signature Algorithm or ECDSA). In particular, the elliptic curve called secp256k1 was chosen (so called according to the classification Standards for Efficient Cryptography or SEC, "International Consortium for the Development of Commercial Standards for Efficient Cryptography" based on elliptic curve cryptography, more information can be found at page 9 of this document), which guarantees high levels of security and short keys, in order to facilitate its use by users.
The secp256k1 encryption algorithm first of all takes care of creating the private key, i.e. a sequence that has the highest degree of randomness allowed by a computer. The result will be a 256-bit integer, represented by 64 hexadecimal characters.
This alphanumeric sequence is called a private key and is extremely important in the Bitcoin system, both because the public key is generated from it, and because owning a private key is equivalent to having the bitcoins associated with the relative address available.
Therefore, since the private key operates as if it were the only secret code useful for opening a safe, this key must necessarily remain secret and kept in a safe place.
Private key example (64 hexadecimal characters) E9873D79C6D87DC0FB6A5778633389F4453213303DA61F20BD67FC233AA33262
The cryptographic algorithm secp256k1, immediately after creating the private key, derives the public key from it, using the elliptic curve multiplication function. Therefore, the public key is uniquely linked to the private key that generated it through an irreversible function which, as mentioned in the previous article, does not allow the key creation process to be easily reversed.
The public key is a 520-bit integer, represented with a series of 130 hexadecimal characters and, unlike the private key, it must not remain secret because it ideally represents the address on which it is possible to receive bitcoins.
Public key example (130 hexadecimal characters) 0450863AD64A87AE8A2FE83C1AF1A8403CB53F53E486
D8511DAD8A04887E5B23522CD470243453A299FA9
E77237716103ABC11A1DF38855ED6F2EE187E9C582BA6
Although it is computationally impossible to derive (today!) the private key from the public one, it has been preferred to subject the latter to further mathematical functions which not only offer the user a high guarantee of security, but also allow the use of a simpler format for daily use.
The bitcoin address, in fact, is obtained by subjecting the public address to multiple hashing procedures performed in succession.
More in detail, the public key is first hashed using the SHA256 algorithm, the result of this processing will be used as input to calculate the hash using the RIPEMD160 algorithm (= RACE Integrity Primitives Evaluation Message Digest or RIPEMD is a function cryptographic hashing and was developed in Belgium in response to the hash function called SHA, developed by the US NSA).
The subsequent result is further subjected to a last encoding using the Base58Check function (used in the Bitcoin system in order to simplify the use of bitcoin addresses, reducing their length and also because it allows for greater integrity checking, including an error-checking mechanism) whose result will be the bitcoin address.
Bitcoin address example (33 characters in Base58)
16UwLL9Risc3QfPqBUvKofHmBQ7wMtjvM
All the previous cryptographic elaborations bring considerable advantages both in terms of usability, since they reduce the public address to only 33 alphanumeric characters, and because they integrate important security functions allowing some automated checks against writing errors of the bitcoin address.
Transactions and privacy
A transaction is basically a passage of bitcoins from one address to another. In order to ensure the highest level of security at all times during this very delicate phase, the Bitcoin system makes extensive use of the cryptographic techniques described in the previous article, such as hashing and digital signature.
Let's see what happens when we want to transfer some bitcoins from one address to another:
When a user A (whom we will call Sender) decides to transfer X number of bitcoins to a user B (whom we will call Recipient) all he has to do is enter the recipient's bitcoin address and the desired amount of bitcoins in the application used as wallet. The software will automatically take care of carrying out a series of operations not directly visible to users, but which are necessary to make the bitcoins transit with extreme security.
First of all, it must be stated that, simplifying a lot, due to an intrinsic property of the Bitcoin protocol, every time a Sender initiates a transaction, he will use the parts not used in previous transactions (UTxO = unspent transaction output). All of these parts, used up to the desired amount, will be sent to the Recipient, any part exceeding the amount due will be considered as remainder.
In fact, each transaction can be represented as a register divided between inputs, containing all the previous transactions from which the bitcoins of one's address originate, and the outputs where the addresses of the recipients will be indicated, including that of the sender if not all of their bitcoins are used.
The output of one transaction will become the input of the next transaction.
Normally the input values are greater than the output ones, since the system is structured to recognize a reward, called fee, to users (so-called miners) who will take care of including this transaction in the Blockchain.
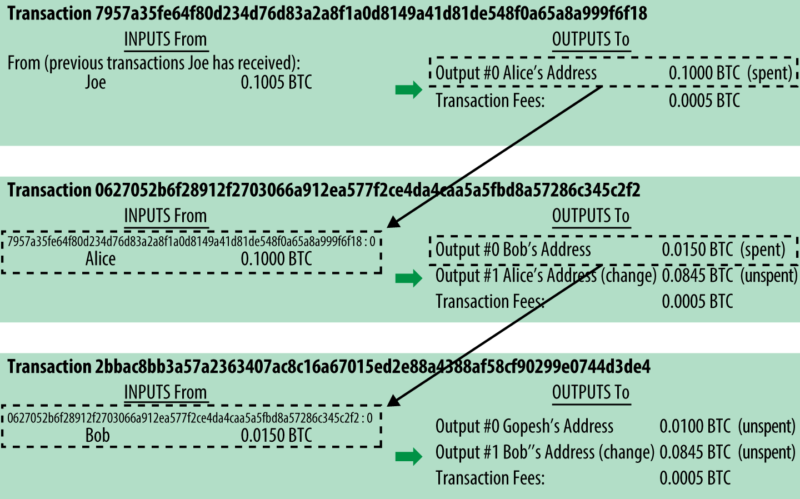
Example of a sequence of transactions, where the input of one transaction becomes the output of the next.
Image taken from “Mastering Bitcoin” by Andreas M. Antonopoulos LLC
(https://bitcoinbook.info – Copyright 2016, Andreas M. Antonopoulos LLC)
After determining which address to send the bitcoins to, the software performs some further important operations.
First of all, using the Sender's private key, the Digital Signature is affixed to the transaction, in order to be able to prove ownership of the bitcoins moved using its public key at any time.
Furthermore, the public key of the Recipient is included in the transaction, so that he alone can be the true beneficiary of the bitcoins sent, verifying the message using his own private key.
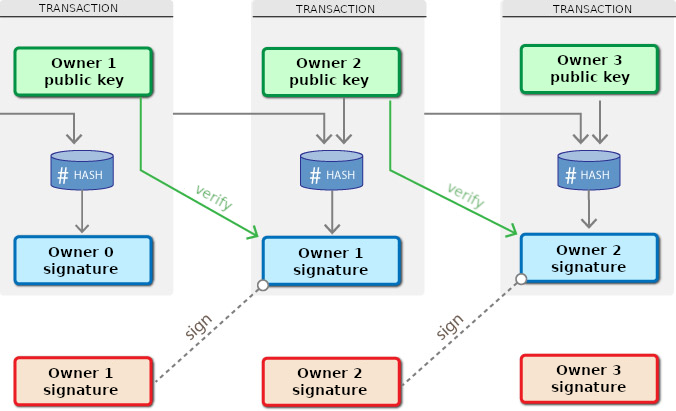
Outline of using public key cryptography in Bitcoin transactions
Each transaction is made up of addresses, amounts, digital signatures and hash values, as well as other data useful for the correct functioning of the system, but in no case are there names or references to the people who are using these bitcoins.
For this reason, the Bitcoin system does not allow a direct relationship between real users and the addresses they use, even if we cannot speak of an anonymous transaction system.
Each Bitcoin transaction, after being approved, is published in a register, called Blockchain, which is public and unalterable.
This means that for each transaction made, there will be an annotation in this register, always visible and available to anyone who wants to consult it.
Furthermore, using additional tools, some of which are freely available online, it is possible to obtain a list of all transactions, as well as other useful information, relating to a specific bitcoin address. On this topic I recommend you to read this excellent article.
Bitcoin Forensics is included in this area, especially for investigation needs, or rather "the discipline that studies investigative and intelligence techniques, tools, methodologies applicable to cryptocurrencies [...] focusing attention on the application of the best practices of computer forensics or network forensics to digital investigations into the world of Bitcoin and the blockchain".
These are just some of the reasons why the Bitcoin system cannot be considered totally anonymous, but it can be defined as pseudo-anonymous, since it guarantees an excellent level of privacy in any case.
Conclusions
Having reached the end of this brief digression (depending on the point of view 😛) on the main cryptographic methods used up to now, with the awareness of having outlined a subject with a thousand nuances, I hope I have succeeded in my intention of arousing and stimulating curiosity about a subject as complex as it is interesting.
Finally, as with the previous articles, I would like to point out some texts (not all, because the subject is complex and there are really a lot of them) that have been a great inspiration for me to write this third part:
Mastering Bitcoin: Unlocking Digital Cryptocurrencies by Andreas M. Antonopoulos, can be considered one of the sacred texts of the Bitcoin topic and you can easily find it for sale online in pdf or paper format, or directly on the author's Github;
Understanding Bitcoin: Cryptography, engineering and economics by Pedro Franco, this is also easily found for sale online;
Cryptocurrencies and bitcoins. A legal analysis by Dr. Stefano Capaccioli, a really interesting text, also by virtue of the fact that it was written by one of the leading Italian cryptocurrency experts as regards the legal framework, with interesting insights on the subject. It can be found for sale online, usually on Amazon.
For any suggestion, criticism, or if you need further texts to deepen the topic, please reach us out.

